I don’t unquestioningly trust default settings when it comes to privacy. Windows 11 is no exception, as it often oversteps by collecting data. However, these specific tools can effectively restrict Windows telemetry without breaking functionality.
3
O&O ShutUp10++
Disable Hidden Telemetry Settings
You won’t find Windows privacy options only on the surface. It also has registry-level telemetry that runs in the background. O&O ShutUp10++ exposes these registry settings that Windows keeps buried.
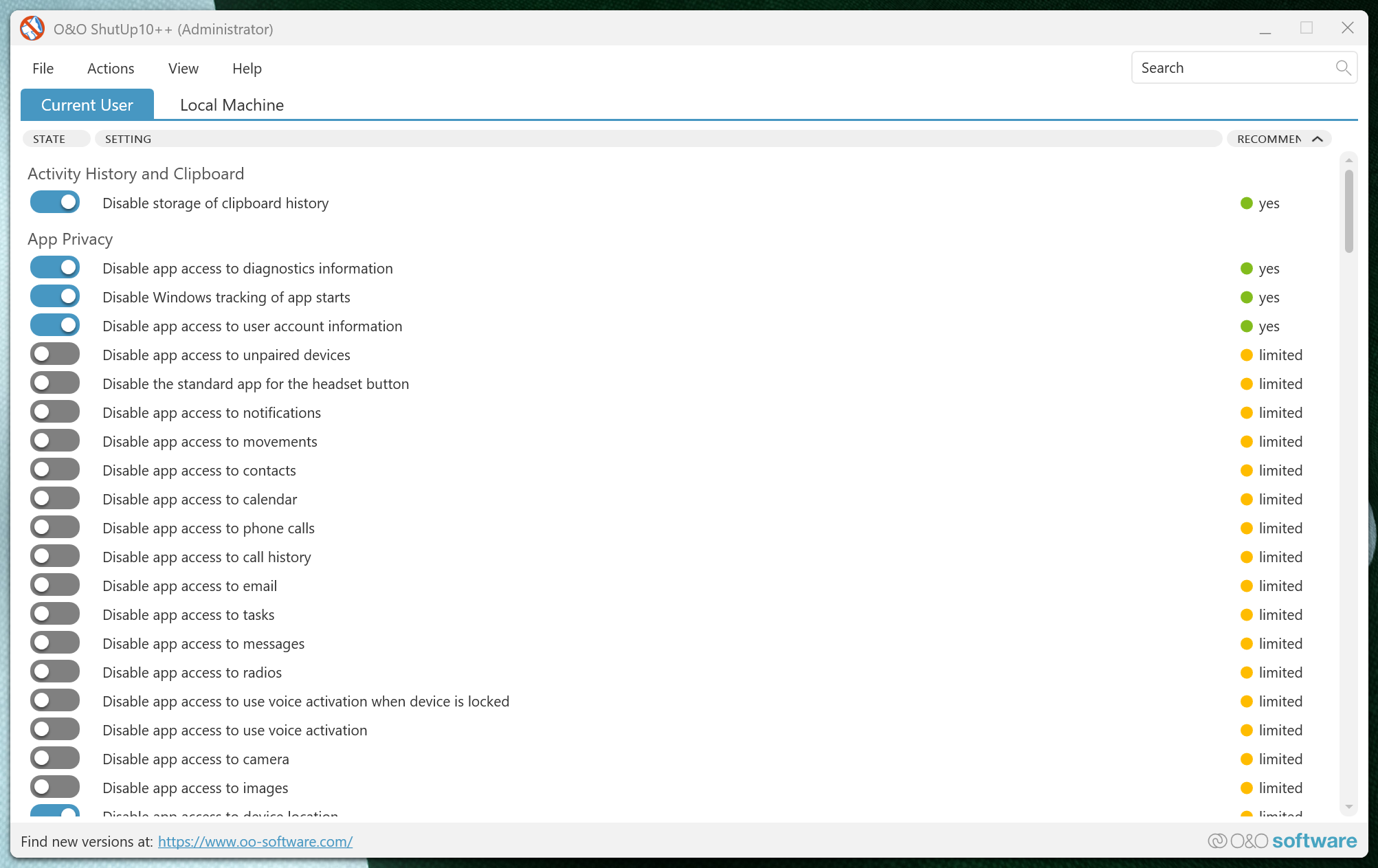
It’s a portable application that provides access to 100+ privacy controls, and categorizes them as Recommended, Limited, or No based on potential system impact.
The interface shows how extensively Windows monitors user activity. You’ll see it in App Privacy settings, which include diagnostic data collection and account information sharing, showing that Windows 11 won’t respect your privacy by default. Each setting includes basic explanations, though some remain technical.
Follow these steps to use O&O ShutUp10++ safely:
- Run the downloaded executable file with administrator privileges.
- Select Current User or Local Machine scope.
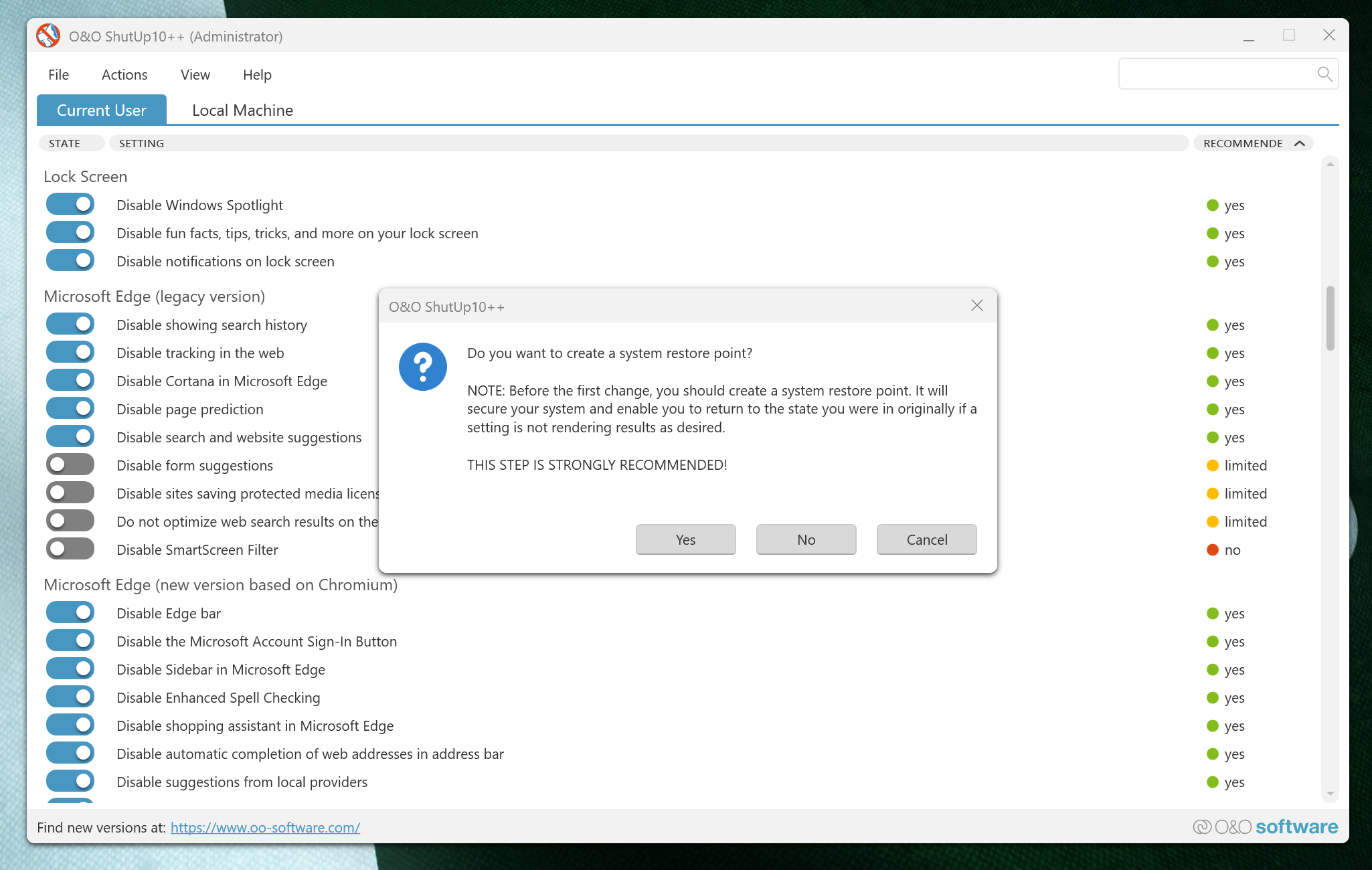
- Accept the system restore point prompt (recommended for safety).
The Recommended category disables common tracking methods without breaking core features. It includes Windows AI, Windows Spotlight content, diagnostic data transmission, privacy, and user behavior collection. The settings under the Limited category are more aggressive but may interfere with Windows functionality or other features.
However, the tool isn’t foolproof. Some settings may cause unexpected issues with specific applications or workflows. Therefore, you should create a restore point before making any changes, as you may need to revert them when functionality breaks.
O&O ShutUp10++ provides broader control than Windows’ standard privacy options, but it requires more technical skill to make sure you aren’t making changes with side effects.
2
Use a VPN
Hide Your Location From Microsoft Services
We can disable location in O&O ShutUp10++, but sometimes that’s not the best option, as other services benefit from it. Microsoft services collect that location data through IP geolocation. Every Windows Update check, OneDrive sync, and Microsoft Store connection reveals your approximate location to its servers.
To avoid that, you should use a VPN. This does not stop Windows telemetry data collection itself, but it masks your real IP address by routing traffic through remote servers. This creates a geographic disconnect between your actual location and what Microsoft’s telemetry systems record.
Your free VPN is just fine for basic privacy needs, though paid services typically offer better server infrastructure and connection speeds. The key consideration isn’t cost but rather the provider’s data handling policies and technical implementation.
Windows Update servers sometimes reject connections from known VPN IP ranges. This forces you to temporarily disconnect for system updates, creating brief moments where real location data gets transmitted to Microsoft.
It is also important to note that DNS-over-HTTPS settings in browsers can bypass VPN DNS protection if configured incorrectly. The reason is that Microsoft Edge, by default, uses Cloudflare’s DNS servers regardless of VPN settings, potentially exposing browsing patterns.
The most effective approach is combinging VPN usage with proper DNS configuration and selective disconnection for essential Windows services that require direct connectivity.
1
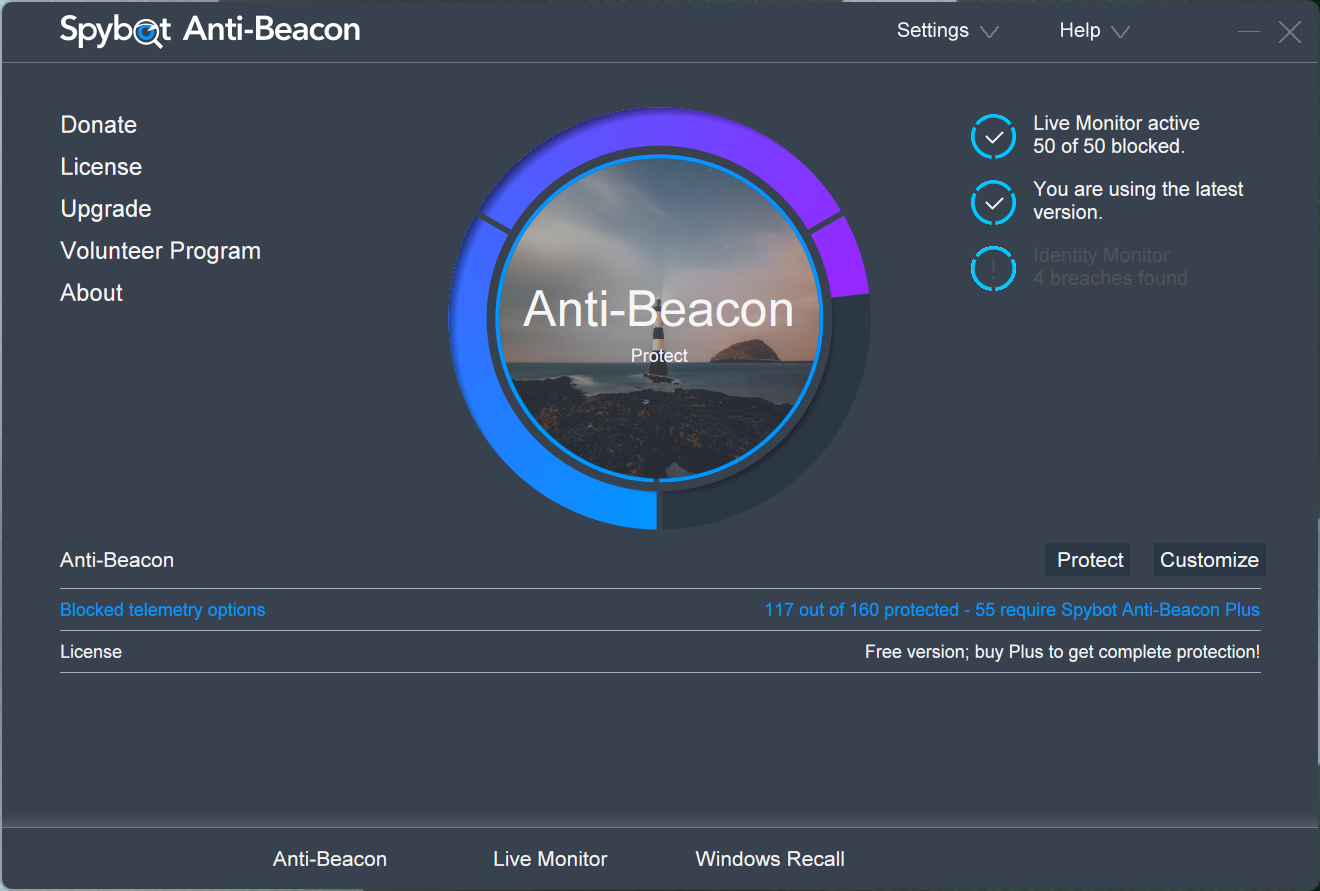
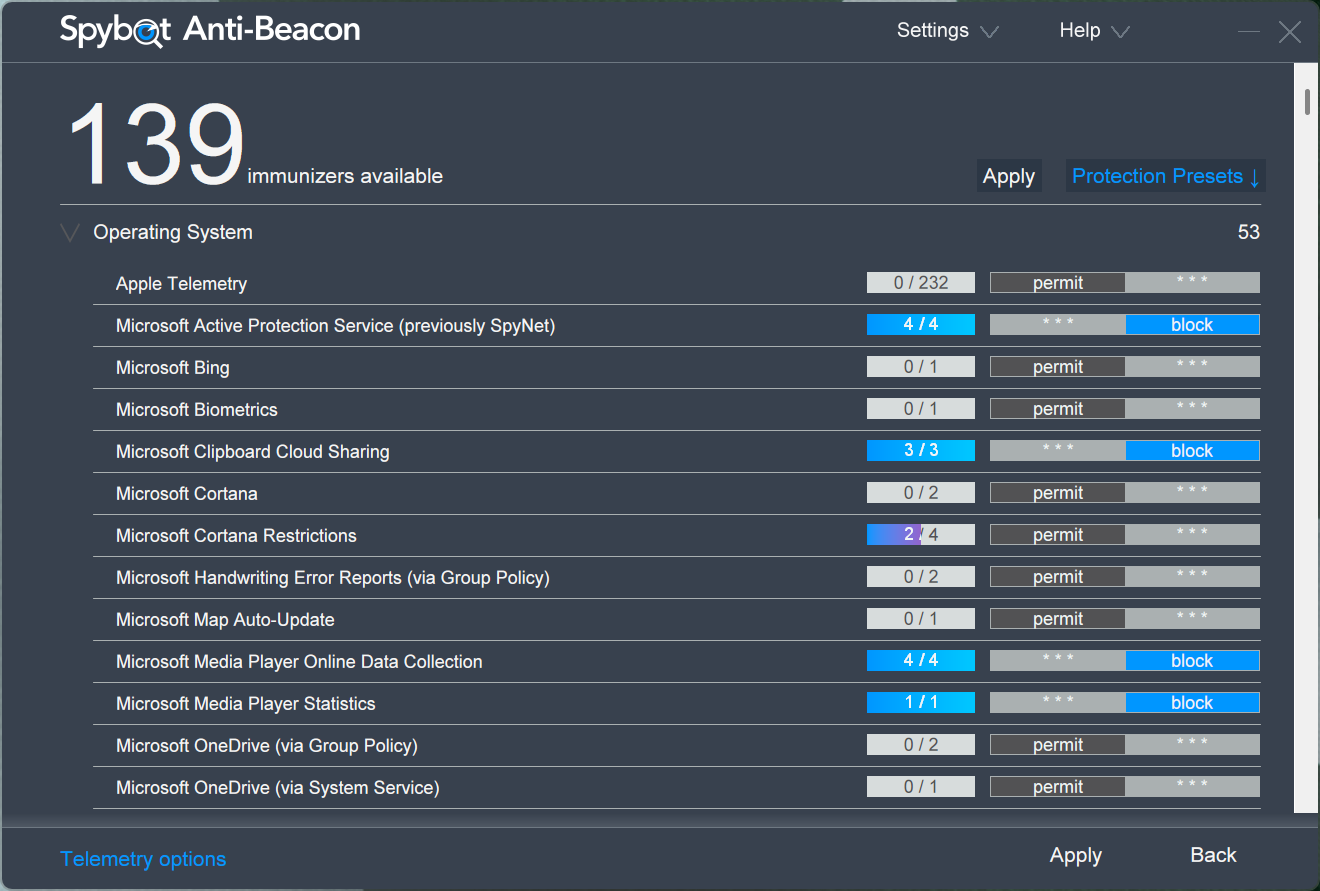
Spybot Anti-Beacon
Block Telemetry Hosts
This tool blocks telemetry at the network level by preventing Windows from contacting specific Microsoft data collection servers. It modifies your system’s hosts file to redirect telemetry requests to localhost addresses.
When Windows tries to send diagnostic data to telemetry.microsoft.com or similar endpoints, those requests get blocked before leaving your computer. This creates a more comprehensive barrier than registry tweaks alone.
Spybot Anti-Beacon targets over 100 known Microsoft telemetry hosts. The blocking happens transparently; Windows continues attempting to send data, but the connections fail. It prevents telemetry transmission without breaking core system functionality, like updates or activation.
Follow these steps to configure Spybot Anti-Beacon:
- Run the installer with administrator privileges.
- After installing, review the list of hosts that you want to block in the main interface.
- Click Apply to activate telemetry blocking.
- Restart your system to ensure the hosts file changes take effect.
The interface shows which telemetry endpoints are currently blocked and allows selective unblocking if needed. If you experience issues with specific Microsoft services after enabling all blocks, the tool provides granular control to resolve these conflicts.
One limitation involves Windows Update behavior. Microsoft occasionally changes telemetry server addresses, requiring Anti-Beacon updates to maintain effectiveness. The tool includes an update mechanism, but there’s typically a delay between new telemetry servers going live and blocking rules catching up.
These tools won’t eliminate every privacy concern, but they create meaningful barriers against Windows 11’s data collection. Microsoft finds new ways to gather your information, so using such tools is one of your limited options to fight back against it.