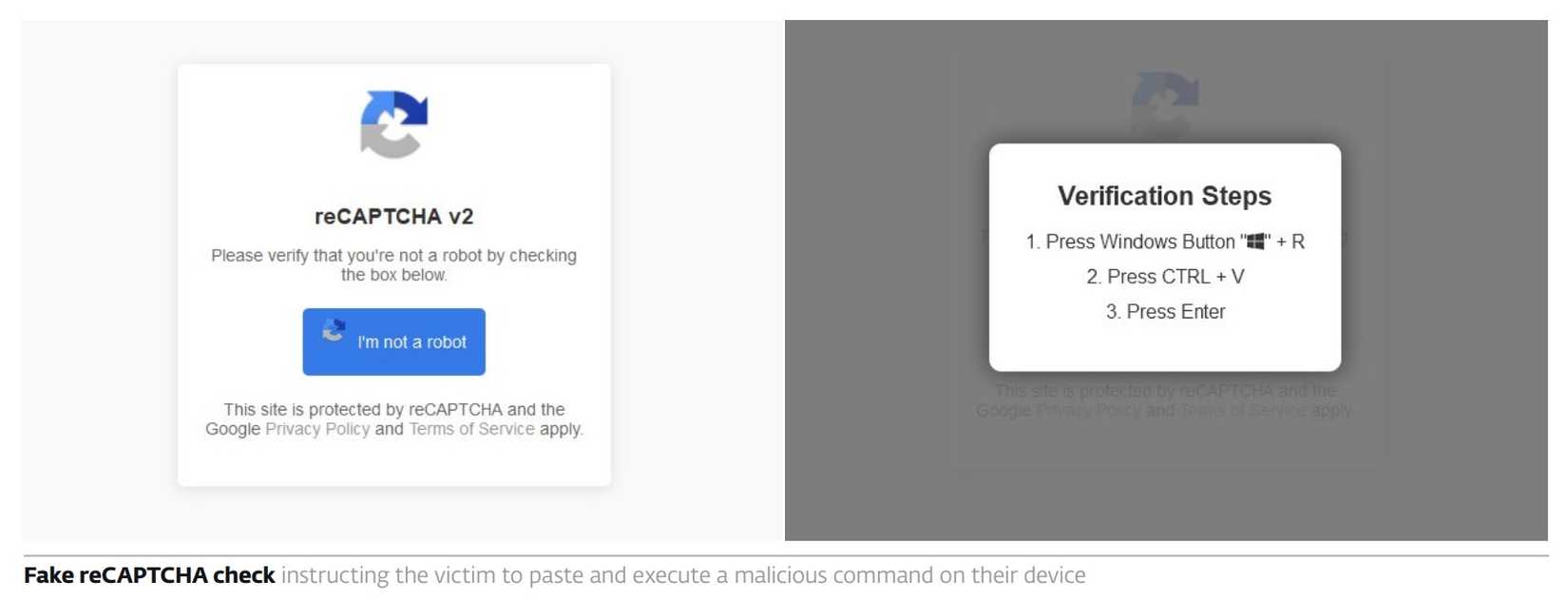
Imagine a webpage that looks like a legitimate CAPTCHA, “browser update,” or a helpful fix-it dialog. The page silently copies a chunk of text or code into your clipboard, then tells you to open Run, Terminal, or File Explorer and paste it there to “verify” or “fix” the page.
When you paste and press Enter, you’ve just executed whatever the attacker put on your clipboard—often a PowerShell or shell command that downloads and runs additional malware. That one simple user action converts curiosity into compromise.
Well, it’s completely real: this is how the ClickFix (and, by extension, FileFix) social engineering security attacks work, why they remain so dangerous, and why they’re not going anywhere soon.
This malware makes you infect yourself
It’s all about the social engineering
ClickFix first appeared in 2024 and has since evolved into dozens of variations. Its premise sounds wild and outlandish, but it makes more sense once you realize how convincing some aspects of it are. You wouldn’t be the first person to say, “There’s no way I’d copy-paste something into my computer,” and you’d be right. But like many scams, you may not actually be the target; consider vulnerable folks using computers, and you get a better idea of why it’s a huge problem.
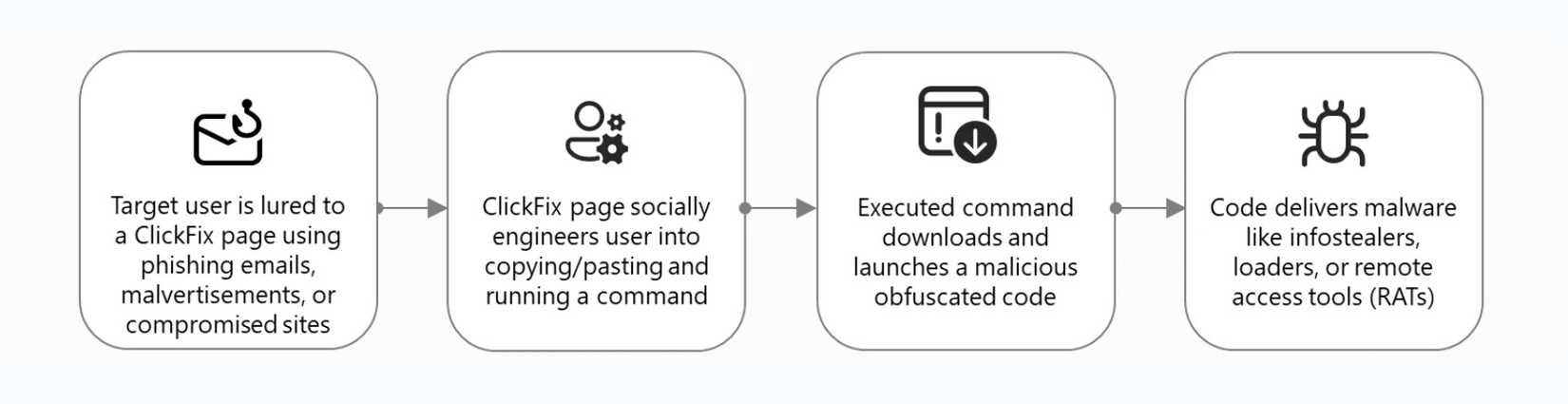
- You land on a webpage that looks like a legitimate CAPTCHA, browser update, or system repair prompt. The page claims something went wrong and tells you to “fix it” by pasting a short command into the Run dialog or PowerShell window.
- Unbeknownst to the user and out of view, the attacker uses JavaScript to sneak malicious code into the Clipboard, containing hidden instructions to download additional malware.
- The victim is advised to open the Run dialog, press CTRL + V, then Enter—executing the malicious command and downloading more malware.
Once the command is executed, anything can happen. The victim doesn’t know what is about to take place on their computer, and the result can be infostealers, ransomware, remote access Trojans, and more, all downloaded directly to your machine.
As you might expect, most ClickFix attacks focus on Windows users, as does the majority of malware globally. However, macOS users aren’t free from risk. Security firms such as Emsisoft and Fortinet have both documented ClickFix attacks focusing on macOS, and highlight that macOS isn’t immune to malware.
How ClickFix starts
Where does ClickFix come from to begin with?
As with most malware, a ClickFix attack typically starts with phishing emails and compromised websites. Researchers have tracked campaigns posing as GitHub, Booking.com, and even Cloudflare verification pages. Fake pages are often delivered via:
- Phishing emails linking to “Fix verification” or “Account validation” pages
- Malvertising and fake browser updates served through ad networks
- Redirects from legitimate but hacked websites
- Social media links pushing fake “patch” instructions
Once the malware is downloaded via one of the above methods, victims receive instructions on how to remove the virus from their systems. However, those instructions actually download further malware, which is often much more dangerous than the original infection.
In that, ClickFix isn’t actually a type of malware; it’s the delivery method. This is why ClickFix is considered a social engineering attack: it convinces victims to do something dangerous. This is also why it’s so effective; because the victim is executing the commands, it skips over most built-in protections in Windows because you’re specifically requesting and executing the malware download.
FileFix uses File Explorer to download malware
Furthermore, there is a newer version of ClickFix known as FileFix.
First revealed in June 2025 by security researcher mr.d0x, this attack uses the File Explorer in Windows to run the same malicious commands to download malware.
So, instead of having to open the Run dialog or PowerShell, the attack directs the victim to open File Explorer. From there, the victim copies the malicious script into the File Explorer address bar and hits Enter, effectively executing the command.
From there, the results are similar to ClickFix. More malware is downloaded, further infecting your machine.
ClickFix isn’t going anywhere
The numbers just don’t lie
The problem with ClickFix isn’t just that it’s sneaky. It’s also that it’s one of the fastest-growing threats, and doesn’t show any signs of slowing down. ESET’s H1 2025 Threat Report found a bonkers 500 percent increase in ClickFix attacks over the course of a single year.
What makes this new social engineering technique effective is that it is simple enough for the victim to follow the instructions, believable enough to look like it might fix a made-up problem, and abuses the probability that victims won’t pay much attention to the exact commands they have been asked to paste and execute on their device — Dušan Lacika, ESET Senior Detection Engineer
Similarly, a Microsoft report identified tens of thousands of instances of people running the malicious code.
Unfortunately, ClickFix has all the hallmarks of an attack that is going to be used repeatedly. And why wouldn’t it? Attackers are clearly seeing enormous success with it, so why change what works?
There are a few more reasons why it’s become the go-to attack:
- Bypasses browser protections because there’s no direct download to flag
- Relies on human trust, not system exploits, so patches alone won’t fix it
- Endlessly reusable — any group can build their own version in minutes
- Looks legitimate thanks to polished fake pages and brand logos
- Cheap and easy to deploy through existing phishing infrastructure
That’s a lofty combination for malware distribution.
There are a few ways to avoid a ClickFix attack
Never paste random commands, that’s for sure
While it sounds like spotting a ClickFix attack is difficult, it’s not impossible.
- Make sure you know how to spot the classic signs of a phishing email, as that’s one of the main ways a ClickFix attack begins.
- Never paste unknown commands into Run, PowerShell, or File Explorer. No legitimate website will ever ask you to do that.
- Treat unexpected “fix” or “verify” pages with suspicion. If something looks off, close the tab and access the service directly.
- Keep your browser and OS security features active. Windows SmartScreen, Defender, and Chrome’s Safe Browsing can still block the final payload. Alternatively, install a third-party security tool like Malwarebytes Premium.
- Use real-time protection and an up-to-date antivirus suite that monitors PowerShell activity.
- Be cautious with shortened URLs and email attachments. Many ClickFix campaigns start from a shortened redirect chain.
- If you have already pasted a command, disconnect from the internet immediately and run a full malware scan. It’s likely that your machine and potentially your credentials are already compromised.
Learning how to spot phishing emails and building a risk-averse approach to security is easily the best way to stay safe. You’re stopping a potential ClickFix attack before it even begins.