Most of the time, your only concern with your home network is whether you can access the internet or not. However, if you were to scan it for vulnerabilities, you might find some more pressing concerns.
Why You Should Scan Your Network
Your home network likely consists of a router that connects all your wired and wireless devices. This setup is known as a SOHO (Small Office/Home Office) network and can have vulnerabilities that hackers may try to exploit. Attackers can attempt to access your network in several ways:
- Exploiting open ports exposed to the internet
- Targeting devices on your local network
- Launching wireless attacks
- Attacking remote work connections (e.g., VPN or RDP)
Regularly scanning your network and addressing vulnerabilities can help protect against such threats. Fortunately, it’s easier than you might think.
How to Scan Your Network: 2 Methods
If you’re scanning your network, you have two options:
- Web-based network scanning tools
- Server-based tools
Web-based tools include websites like Pentest Tools. These tools let you quickly scan your public IP address for any open ports that hackers can exploit. However, this is only a surface-level scan, at least until you pay for these services. Web-based tools like Pentest Tools can only scan what’s visible from the internet—not your internal devices or Wi-Fi clients.
If you want more information, you will need to use server-based tools like Nmap, which operate on an external server and scan your network from the outside. Nmap is open-source, free to use, and is often used by hackers to scan a network before attempting to hack it.
Pentest Tools
If you’re just getting into penetration testing or want a simple overview of your network without having to spin up a Linux server, Pentest Tools will suffice.
- Locate your external IP address without using a VPN and record it. You can find your external IP by Googling “what is my IP address” or via sites like What Is My IP?.
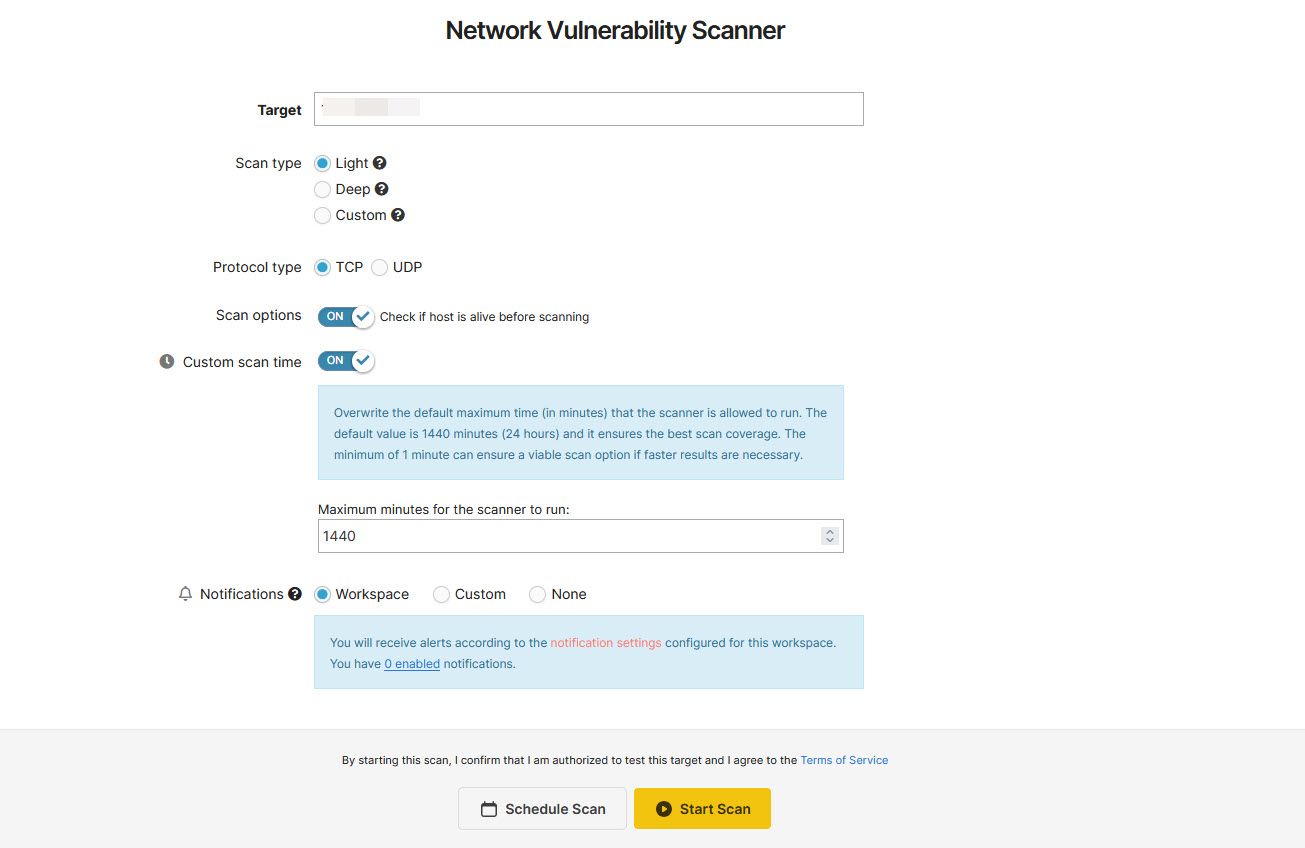
- Open the Network Vulnerability Scanner on Pentest Tools, copy-paste your external IP address in the Target field, and click the Start Scan button.
The results page will show you all the network information and open ports an attacker can pick up by scanning your public IP address—a big reason why you shouldn’t publicly expose it. However, the results of the light scan available to free users are only good for finding popular ports that might be open on your network by default. Running a deep scan, which scans a significantly higher number of ports, can cost up to $85 a month; however, considering the site uses Nmap to run its scans anyway, you’re better off learning Nmap if you need more in-depth results.
Nmap
If you want more in-depth results, Nmap (Network Mapper) is a better choice. Installing and running Nmap requires some technical knowledge, but a Windows GUI version is available.
Download: Nmap
Install Nmap on your Windows, macOS, or Linux device. You can then scan other devices on your home network:
nmap -sT [your external IP address]
This command scans all devices on a typical home subnet for open TCP ports.
However, the best way to run Nmap is via an online Linux server. Running Nmap from an external server allows it to scan your network from the outside, exposing open ports, vulnerabilities, and services that can potentially be exploited. When run locally, Nmap can scan other devices on your network—such as your router, smart devices, or other PCs—to identify open ports and services. It won’t reveal what an outsider sees unless it is run from outside your network.
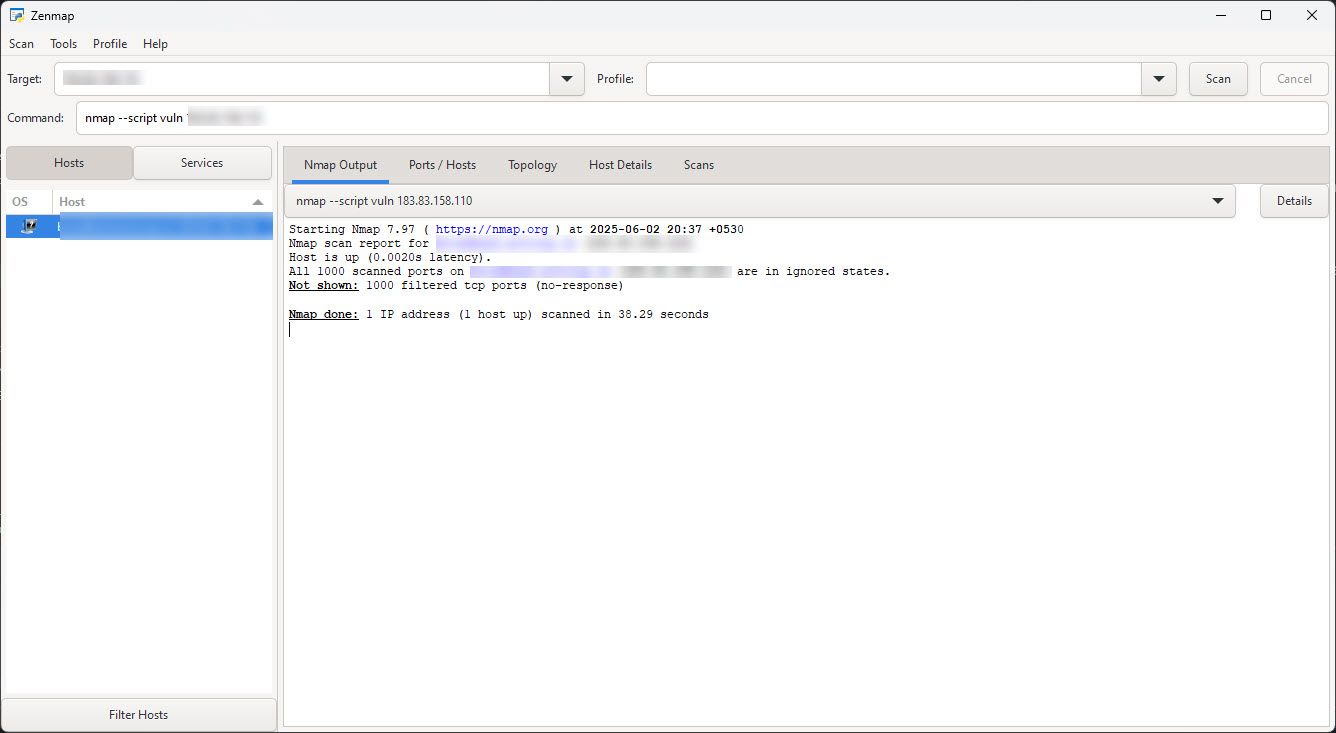
Once you’re set up, run the sudo apt install nmap command in the terminal to install Nmap. Then scan for vulnerabilities on open ports:
nmap –script vuln [your external IP address]
The problem with using Nmap from an external server is that you’ll either need some technical expertise with Linux or spend money to get a server up and running. You can hire a Linux server on websites like Linode or Vultr for $5 and $2.50, respectively. These services allow you to sign up using an email account and provide access to a Linux machine with substantial resources after completing the verification process. Alternatively, you can try running Nmap on Linux on another machine and have that scan your network. Just make sure the scanning machine isn’t using your router to connect to the internet, as that can confuse the process.
Running scans from a VPS means sharing your home IP with a third-party service. Always follow the VPS provider’s terms of service, and never scan networks you don’t own or have permission to test.
This is a limitation of scanning a network while using it—you never get to see the intruder’s perspective. The way your network behaves internally and externally is different. Unless you can see the same vulnerabilities that a hacker can exploit, you can’t fix them, and they’re only visible from outside the network. This is why many security enthusiasts or individuals who want to test their network strength set up a lab with at least one machine running Linux, connected to the internet via an external connection.
Patch the Holes and Harden Your Wi-Fi Router
Regardless of the scan you run, you’ll see information about your router, ISP, current location, open ports, and, if you’re using Nmap, any vulnerabilities you might be exposed to. Typically, you’ll find a series of commonly used open ports:
- 80 (HTTP)
- 443 (HTTPS)
- 53 (DNS)
- 3389 (RDP)
- 22 (SSH)
- 23 (Telnet)
Not all open ports are dangerous, but they should be understood. Open ports allow external services to communicate with the software running on your devices, like PCs, smartphones, smart TVs, and even your router itself. However, simply shutting down all open ports isn’t a practical solution, as it’ll hamper your internet connectivity.
Common ports like 80 (HTTP), 443 (HTTPS), and 53 (DNS) should be left open. However, if you have any open ports used by third-party applications or OS features, such as RDP (3389), SSH (22), Telnet (23), and FTP (20 and 21), you should consider closing them, depending on your network usage.
If you need a particular port open for whatever reason, you can hide it from hackers scanning your IP or router for vulnerabilities. At other times, you can open the specific ports required, then close them again to secure your network. There are many legitimate uses for RDP, SSH, Telnet, and FTP, and closing those ports will stop those protocols from communicating with external services.
As you can see in the scan results from the previous section, all ports that Nmap and Pentest Tools’ network scanner examined on my network were closed. More specifically, they were in a “filtered state” where a network scanning tool can’t confirm whether the port is open, closed, or filtered.
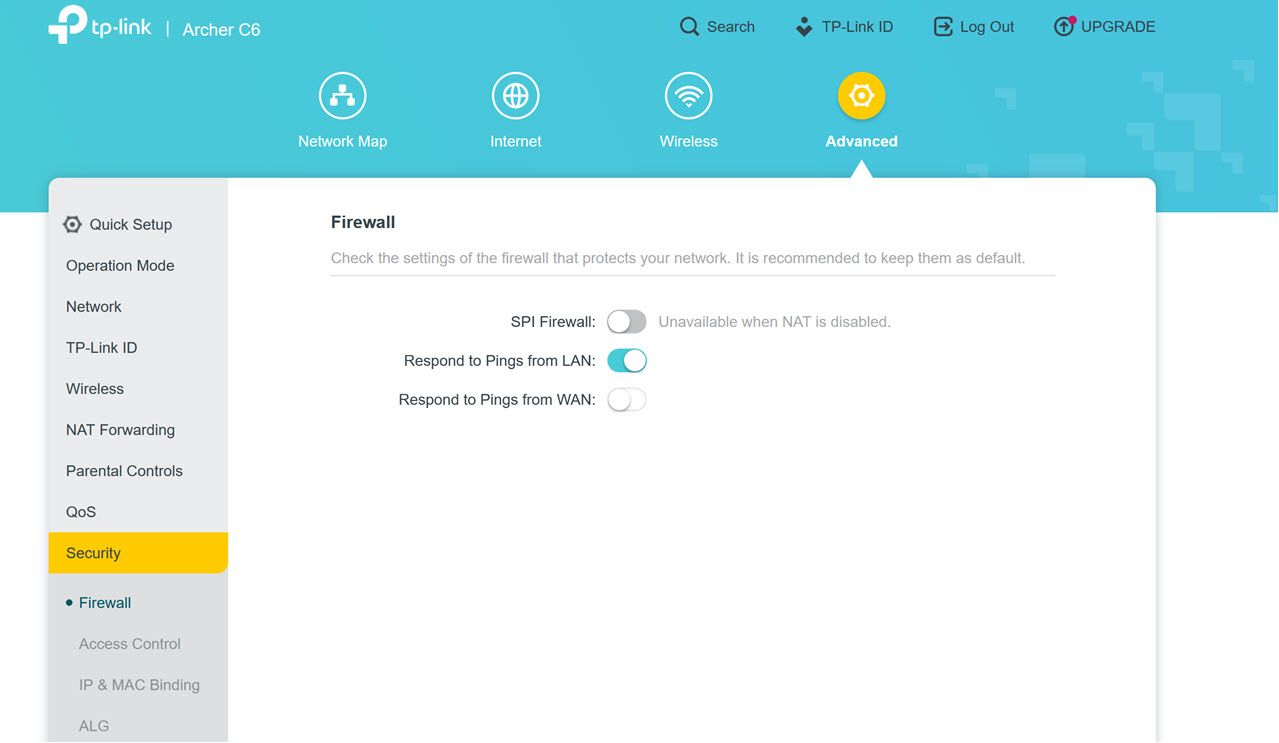
You can achieve this by fine-tuning firewall settings on your router. If you see an option to disable pings from WAN, enable it right away. This tells your router’s firewall not to respond to pings coming from the internet, meaning it won’t show up when hackers run mass IP scans.
This brings me to the next most important way you can protect yourself: your router settings. Hardening your router against attacks is one of the first steps you should take when setting up a new router for optimal results. However, some Wi-Fi router settings are best left disabled.
The exact router settings you need will vary based on your router, but the following list of settings is a good place to start:
- Enable the router firewall
- Disable remote access features
- Disable all port forwarding entries
- Disable UPnP (Universal Plug and Play)
- Change the default router access credentials
- Use WPA3 wireless encryption if possible
- Update your router’s firmware frequently.
Scanning your Wi-Fi network for security loopholes might sound complicated, but with some simple tools and a little bit of research, you can tune your network to be a lot more secure.