Windows File Explorer provides a ton of options to change how you view your files. What you might not know is that a critical option is disabled by default, despite being vital to your system’s safety.
File Extensions Are Important
File extensions are three or four-letter suffixes that appear after the final period of a file name, such as .txt, .exe, or .pdf. These extensions act as identifiers so the OS (and you) can tell at a glance what kind of file they are.
Windows uses file extensions to determine which app should launch when you double-click a file. For example, an .exe file will launch an application, while a .docx file will open a Word file in Microsoft Word. A lot of programs save files in their own unique file extensions, which can then only be opened in that program (or a compatible third-party tool).
A key advantage of being able to see file extensions is the ability to spot potentially dangerous files. Certain extensions like .exe, .bat, .cmd, .vbs, and .scr (among others) can be dangerous files designed to run malicious code on your system. Such files often employ file extensions used by legitimate Windows tools and programs, so spotting them can be tricky.
Despite their importance, file extensions are hidden by default in all modern versions of Windows. This is done to create a cleaner user interface within File Explorer. However, malware creators often use hidden extensions to disguise malicious executable files as seemingly harmless documents to trick you into running malware on your PC, so it’s much better to have them visible.
Showing File Extensions on Windows
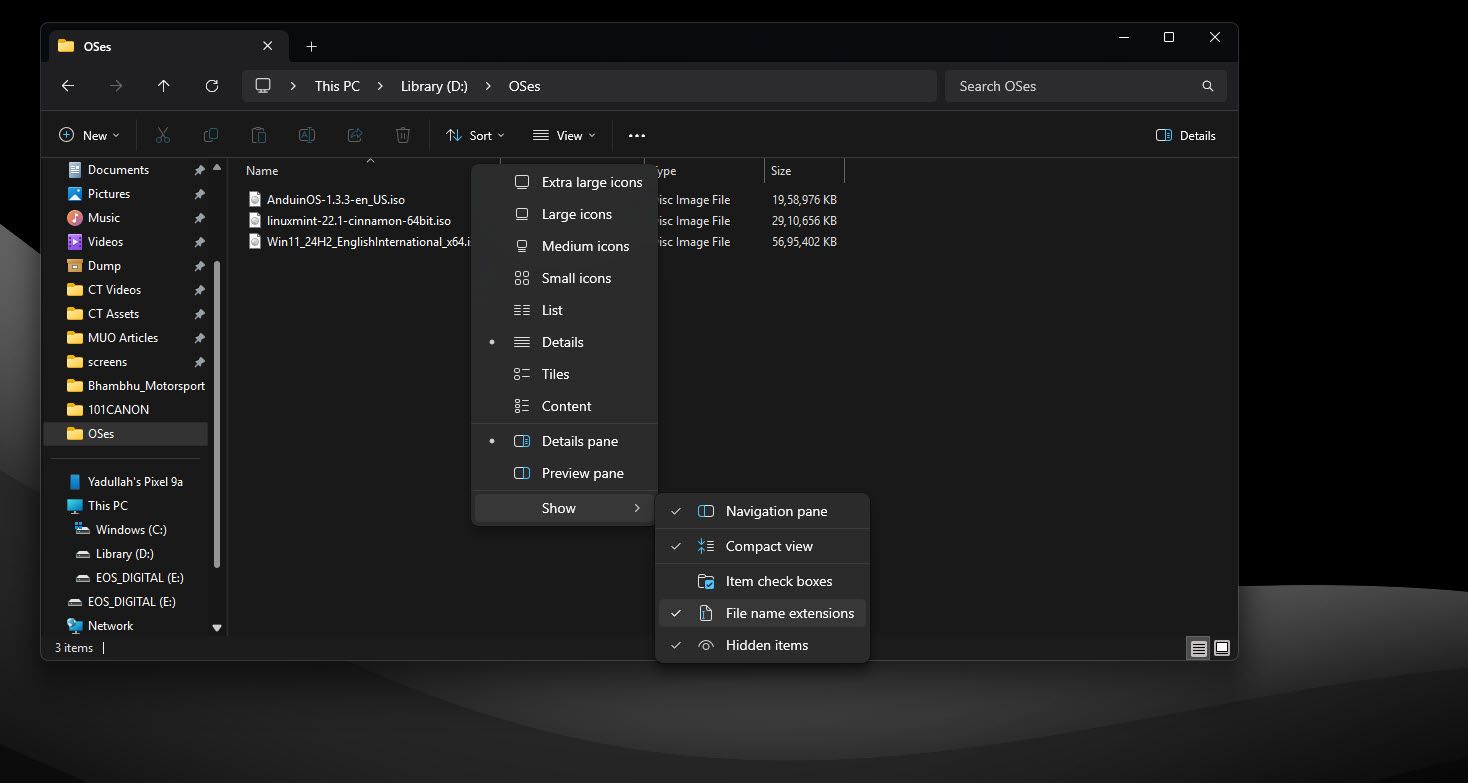
Thankfully, enabling file extensions on Windows takes only a few clicks. On Windows 11, simply open File Explorer by using the Windows key + E keyboard shortcut, click View in the top bar, hover over Show, and select File name extensions. You should start seeing file extensions for all files saved on your PC.
If you don’t see the top bar in File Explorer, you can also enable file extensions from Windows settings. Follow these steps:
- Press Windows key + I to open Windows Settings. Head to the System tab and select For developers.
- Expand the File Explorer section by clicking it, then make sure the Show file extensions slider is turned on.
Particualrly if you’re using an older version of Windows, the Control Panel also comes in handy for enabling file extensions:
- Open the Start menu and search for Control Panel. Click the corresponding option.
- Change Category to Small icons if needed, then choose File Explorer options.
- Under the View tab, make sure that the Hide extensions for known file types option is unchecked.
You can also enable file extensions by making a small change to the Windows registry, but I recommend avoiding this. The three methods above should work on any version of Windows you’re using in 2025, and are much less prone to error. However, if you want a quick way of enabling file extensions, simply run this command in either the Windows Terminal or PowerShell:
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced /v HideFileExt /t REG_DWORD /d 0 /fThis command will add the required entries to the Windows registry that tell File Explorer to start showing file extensions. Make sure to refresh File Explorer using the F5 key to see the changes.
How Attackers Exploit Hidden File Extensions
As mentioned, hackers often exploit hidden file extensions on Windows to disguise malicious files as innocent ones. For example, a file named image.png.exe will appear as a PNG image file in File Explorer with file extensions hidden, when in reality it’s an executable file that can run malicious code or malware when launched.
This technique is called a “double extension attack” and is the most common type of extension attack you’ll see. Thankfully, as long as file extensions are enabled, these malicious EXE files are pretty easy to spot and avoid. However, this is far from the only technique that tries to use hidden extensions to confuse you. Some other popular methods include:
|
Technique |
Example |
Description |
|---|---|---|
|
Right-to-Left Override (RTLO) |
image[RTLO]gpj.exe appears as image.exe.jpg |
Attackers use the Unicode character U+202E to reverse the file name. |
|
Whitespace Padding |
document.pdf[insert 100 spaces].exe |
You can place multiple spaces between the fake and real file extension, so the real extension gets pushed off-screen even when file extensions are enabled. |
|
Icon Manipulation |
document.exe file with a PDF icon |
This is a simple technique where a criminal swaps out the icon of a malicious file for something more familiar, such as a PDF or JPG icon. |
|
PIF Files |
document.pif |
PIF file extensions are automatically hidden by Windows, even if file extensions are enabled. That said, PIF files are rarely used in modern Windows versions. |
As you can see, there are plenty of tricks attackers can use to trick you into running a malicious executable you might think is an image. However, by spending just a few seconds enabling file extensions on Windows, you can catch these traps before accidentally launching any malware on your PC.

Related
9 Default Windows Settings That Make Your Life Harder
Stop settling for a subpar Windows experience.
File extensions help identify what type of file you’re dealing with, but Microsoft’s choice to hide them by default in File Explorer opens the door for fraudsters to disguise malicious files. Don’t fall for these tricks. Enable file extensions and always double-check a file before opening it, especially if it came from the internet or you didn’t ask for it.